Is a VPN enough for your business?
written by Anthony Arrington 11/17/2022
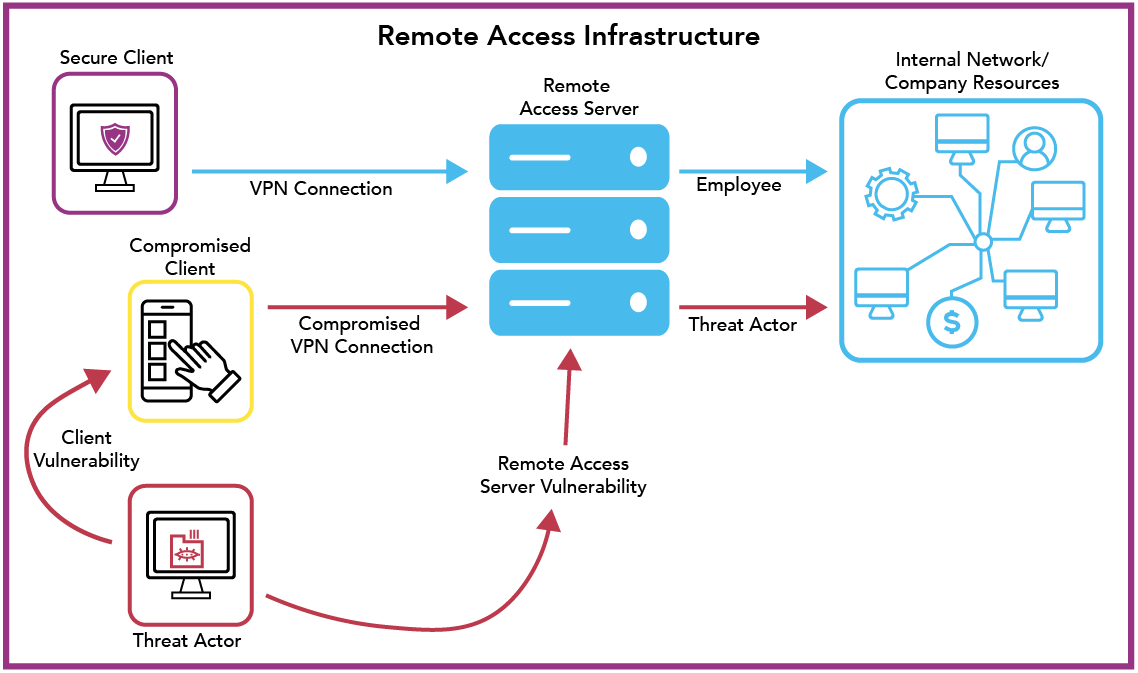
We are in a technological era where the average employee partakes in telework in some fashion. Whether your employees are fully remote, hybrid, or just checking their webmail from the Bahamas, a VPN is an important factor in setting up secure methods of access for your employees. This is true for small businesses as well as fortune 50 businesses. Here’s the kicker, a VPN can add to your security posture, but there are other important factors that need to be accounted for to ensure the VPN your remote employees are leveraging remains a secure method of access. If you want to know whether your company’s remote access infrastructure is accounting for a few big security pitfalls of remote access, read on.
VPN Client Security
One of the first factors of remote access that should be considered is the client machines that will be leveraging remote access to access internal company resources. While a VPN can provide secure transportation for data to and from the company network and client machine, if the client machine is not being secured properly itself, malicious actors now have a potential foothold into your company network by leveraging remote access capabilities maliciously. When I talk about remote access client machine security, one of the most important tools I am referencing would be simply adding an antivirus (AV) or endpoint detection and remediation (EDR) agent on all endpoints that would leverage the company’s remote access. This will allow the company to predetermine if a machine should be allowed access. Even if it is not viable to place an AV or EDR agent on all client machines due to bring your own device (BYOD) policies, NIST recommends that a tiered access solution be put in place that would segregate non company managed assets from company managed assets. This allows everyone to access limited resources regardless of location and hardware, while placing special emphasis on sensitive data only allowing access to assets the company controls and manages.
Securing Your Remote Access Server
Now that we have some controls in place to ensure the clients leveraging remote access are up to par, what about the remote access servers themselves? Well, this depends on the company. Some smaller companies may leverage service providers for remote access, while bigger companies may choose to build out this infrastructure themselves. Either way, it’s important to understand the security controls in place around the remote access server. The remote access server is the point that all clients will traverse to gain access to internal company resources. While AV and EDR can provide detection and remediation, a remote access server is a public facing server that anyone globally can attempt to gain access to. What this means is detection and remediation is a good start, but it may also be too little too late. If the remote access server is compromised, then effectively any data that traverses this server is also compromised. In order to prevent this, it is good to take a proactive approach to securing a company’s remote access server. This is achievable by leveraging security testing against a company’s remote access server as well as the infrastructure it is connected and has access to. Security testing can range from simple vulnerability scans to full teams of penetration testers simulating attacks on company infrastructure to find vulnerabilities that automated scanning may miss. Having a plan in place to find these vulnerabilities, before the bad actors do, can reduce the risk a company takes on by providing remote access capabilities.
Let’s Talk About Your Mindset…
The final factor of remote access we will talk about is mindset. Providing remote access to employees is beneficial to most businesses and the employees. Not only was remote access valuable for combatting covid the past few years, but it has also provided accessibility to those that were unable to commute to an office or company site for various reasons. Overall remote access has provided some positive benefits to all industries, but we must not make the mistake of dismissing remote access as a technology we can set up and forget. It is important we recognize the dangers of having a globally accessible route into an internal company. Remote access clients should always be treated as if they have already been compromised. Remote access presents challenges that are not present in a traditional office environment. This Is because while client machines may have security controls in place, we cannot enforce them 24/7 when they are not on the network 24/7 which is often the case with remote access client machines. A common example is an employee who works remotely goes on a long vacation and does not power on their machine for 2 weeks. During this 2-week period there were multiple vulnerabilities and patches announced and therefore pushed out to all company assets. If the employee’s machine is not on it will not receive those patches until a later date and there is not much a company can do about that. It’s not anyone’s fault, but it is still an issue. While you may not be able to update client machines that are inaccessible, a company can implement security controls that enforce compliance before allowing remote access. By creating a baseline security configuration that all assets must be compliant with, we can now restrict access to only machines that meet this compliance standard. While it does not fix the issues of ensuring 24/7 compliance on remote assets, it does remove a lot of the risk associated with having company assets offline for extended periods of time by forcing them to come into compliance before accessing internal company resources.
I would like to mention that the topics covered here can be attributed to NIST Special Publication 800-46, Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security. If you or your company is concerned with your current security posture when it comes to telework and remote access to internal company resources, NephōSec Cloud Security provides vulnerability scanning services as well as penetration testing services. NephōSec can provide detailed reports that will give you a clear picture of how your remote access infrastructure stacks up against the contemporary tactics, techniques and procedures (TTPs) in use by malicious actors.
Sources:
- Souppaya, Murugiah, and Karen Scarfone. “Guide to Enterprise Telework, Remote Access, and Bring Your Own … – NIST.” NIST.gov, National Institute of Standards and Technology, July 2016, https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-46r2.pdf.